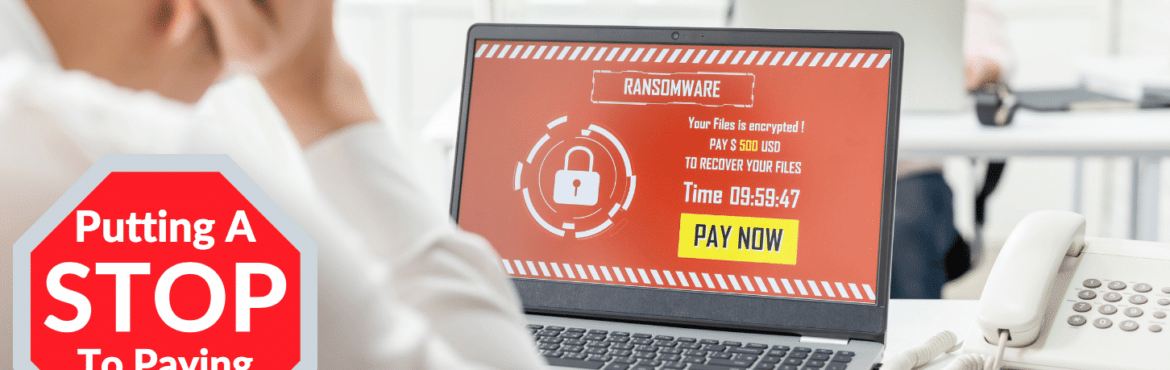
Due to multiple cyberattacks four years ago, cybersecurity was definitely a hot topic during this year’s presidential election. With three weeks leading up to the big day, Microsoft, working with law enforcement groups, disabled one of the largest hacking operations, an effort run by Russian-speaking cybercriminals. This action could have set the path to ensuring what is […]